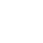If an executive asks you why digital governance matters, tell them $8.4 million a day, plus a $30 million lump sum. If that doesn’t get their attention, look for another job. If it does, here’s how you can explain those numbers.
MGM recently became the victim of a major cyberhack, an event that cost the company a reported 8.4 million a day until it was resolved, plus $30 million in ransom that MGM reportedly paid to the hackers. It was such a big financial hit that analysts are now saying the event may impact MGM’s overall credit rating, and at one point following the incident, MGM’s stock declined more than 13 percent since the Sept. 11 event.
Digital Governance MATTERS.
MGM is just the latest (very public) example. Leaders at companies big and small fail to understand that digital hacks can have very real financial and reputational impacts.
Let me say for the record that I have some friends on the MGM digital team, and they are total pros. They have taught me a lot and are great people. Not surprisingly, they were NOT the reason for the breach.
Nope, this major hack that cost the company tens of millions of dollars was made by a practice called “vishing” – think of it like “phishing” with your voice instead of a fake email. (There’s also a thing called “smishing,” which is phishing via text). The scammers basically found the name of an employee, got enough information about that employee that they could pose as them in a call to the IT help desk and then conned the helpdesk into giving them access to the employee’s accounts. Easy peasy. Tens of millions of dollars came down to one employee’s identity being inadequately protected. This tweet really sums it up.
Lessons To Be Learned From This Incident
-
Password security MATTERS – and it’s more than just your password to get logged into the network via VPN. Companies have a huge blind spot when it comes to passwords because of the proliferation of systems employees are logging into on a daily basis. Most companies have extremely stringent password protocols for that one network password, but the days of one password to rule them all are over. The truth is that most employees have a few dozen work-related passwords (more if they work on social), and only a handful of them are really managed by anyone, particularly IT. Third-party apps are another way that hackers often gain access (basically by breaking in through a less-secure third-party platform you’ve authorized to connect to your main network).
-
Companies need to understand the fuzzy line: The days of working 9 to 5 and then going home and leaving work at work are over. People work remotely. People check Facebook at work. People reuse passwords because who can remember them all? There is a great fuzzy line between the work and personal digital lives of employees, and most companies still pretend this is not the case.
-
Employees need to play their part: Even though I just said IT doesn’t manage enough, the truth is that your entire employee base needs to be vigilant. Scammers are really smart. They are producing more and more legit-looking phishing emails. They are getting more sophisticated. I am an expert in this space and I still occasionally get duped. But most companies are not thinking about making their password security more sophisticated. The truth is that your IT department can require that network password to be eight characters and include uppercase and lowercase letters and a symbol and a number, but that is only part of the picture if the employee’s password for every other system is “company123” or worse yet “password.” Also, they can ask you to change that one password every three months, but how often do you change the others? Biometrics may help with this eventually, but not yet.
-
Your helpdesk needs training: Especially with the outsourcing of most helpdesks overseas, it’s easier for scammers to pretend to be employees because they are often talking to people who are not native English speakers. Remember also that with LinkedIn being LinkedIn, it’s really easy for scammers to find the names, titles and other information about employees. Helpdesks need to be aware of vishing, and protocols for receiving information or access may need to be more stringent.
-
IT needs to understand the tie between personal and work social: Particularly with social media employees, IT departments need to know that a person’s personal Facebook password or LinkedIn password is the password that grants them access to the company’s account. This is because of the way admin rights are granted to users on those platforms. Instead of logging in using a username/email and password combination like you would on Instagram, Facebook and LinkedIn accounts still grant someone access to the page via their personal account. This means that if someone’s personal password is password123, that’s all a hacker has to crack to get into the company’s Facebook page. This is something both Meta and LinkedIn should consider as I think it’s a major security flaw built into both of these platforms. It is also how an awful lot of hacks happen. Think about this: If a hacker gained access to your company Facebook page this way, they could then remove all the admins and take control of the account. It happens. Don’t think it won’t happen to you.
It breaks my heart when I see headlines like the ones I’ve been seeing about MGM. First, I know the pain the entire organization must have felt, not to mention the all out fire drill of trying to get control of everything back while also managing the PR firestorm. But you know the saying… never let a good crisis go to waste. If you read anything in this post that made you go “oooooh,” now’s the time to start addressing it – not after your company is the one making headlines.
If you want to read more about the MGM hack, here are some good articles:
-
A full timeline of the MGM Resorts cyberhack (Cybersecurity Hub)
This article was originally published here.